More GOOGLE $EO Rabbitholin' fun...
Threat Hunting & Rabbitholin' are a lot like the "Choose your own adventure" books we had as kids (late 70s/early 80s). Before access to video games, Internet & most modern electronics we had books/words and our brain. We were the CPU and we processed the programs/code (books) but made it dynamic (and arguably more valuable) with our logic, reasoning and choices made in order to get the "best" ending or result.
Let's use the same methodology used in "experiencing" the old-school CYOA books to rabbit-hole for threats. We will also use similar methodologies from the last BLOG POST "GOOGLE $CAMS: $EO VooDoo".
1. SEARCH GOOGLE FOR TOPIC OF INTEREST. Here's the first choice you have in this adventure! Let's try to find links to a rogue Android APK download for a "Wells Fargo" branded mobile application (using the search terms below along with the PAST 24 Hours search parameter):
download wells fargo bank app android
2. EXAMINE THE GOOGLE SEARCH RESULTS ...
When checking the results you should be looking for any anomalies and/or anything that doesn't look 'normal'. In our results...the 2nd result looks odd...
SEARCH RESULT:
[DOC] Ellens emoji exploji itunes - 18 hours ago
CLICKING LINK LEADS TO:
hXXp://wffw[.]jenniferashe[.]net/BQ
3. CLICK ON THAT LINK!!
Be sure you are using a safe environment to do your research and not infecting yourself unintentionally. Unsafe Rabbitholin' should be avoided unless that is yer intent! On to the clickin'...
Upon clicking the link we are presented with a familiar looking animated loading splash page (from our previous BLOG POST):
Meanwhile, in the background, the browser is being redirected to multiple websites (through a redirect chain) where eventually we will end up on a landing page of unknown intent, content & threat level. Guess we'll find out any second now!
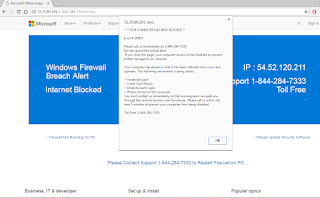
OMFG!@#$ "Your Browser have been hijacked or hacked."
-------------------------------------------------------------------------------------
FINAL LANDING PAGE:
hXXp://www[.]plaza-place-on[.]us/
SCAREWARE & FAKE TECH SUPPORT SCAMS!
 |
| -CLICK TO ZOOM- |
WARNING! Your Hard drive will be DELETED if you close this page. You have a ZEUS virus! Please call Support Now!. Call Toll-Free:+1-(866)-331-7691 To Stop This Process"
NEW DATA POINTS OBSERVED:
Exploit.SWF.db
0x8024402c
1-(866)-331-7691
www[.]plaza-place-on[.]us
4. REVIEW THE REQUEST SEQUENCE/REDIRECT CHAINS
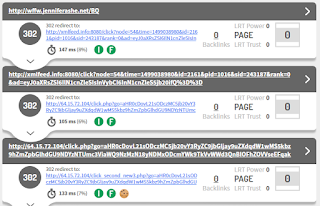
We will now examine the sequence of events & connections from the initial request to the final loading of the view from plaza-place-on[.]us.
302 hXXp://wffw[.]jenniferashe[.]net/BQ
IP ADDR: 95.211.230[.]116
302 hXXp://xmlfeed[.]info:8080/click?
IP ADDR: 216.172.56[.]21
302 hXXp://64.15.72[.]104/click[.]php?
IP ADDR: 64.15.72[.]104
302 hXXp://64.15.72[.]104/click_second_new3[.]php
IP ADDR: 64.15.72[.]104
302 hXXp://go[.]quali-bid[.]com:17777/click[.]php?
IP ADDR: 64.15.72[.]46
200 hXXp://www[.]metal-rewards[.]us/
IP ADDR: 198.54.115[.]15
200 hXXp://www[.]plaza-place-on[.]us/
IP ADDR: 198.54.115[.]15
NEW DATA POINTS OBSERVED:
UNIQUE HOSTS
wffw[.]jenniferashe[.]net
xmlfeed[.]info:8080
64.15.72[.]104
go[.]quali-bid[.]com:17777
www[.]metal-rewards[.]us
www[.]plaza-place-on[.]us
UNIQUE IP ADDRS
95.211.230[.]116
216.172.56[.]21
64.15.72[.]104
64.15.72[.]46
198.54.115[.]15
!!!!!! CHOOSE YOUR OWN ADVENTURE TIME !!!!!!
So...where do we go from here? We definitely have several NEXT PIVOT data points, and where you begin is totally up to you (with the goal being, of course, to not get lost in the rabbit-hole). Today, I will start with WHOIS/IP Lookups of the the INITIAL REQUEST URI and the FINAL LANDING PAGE presented and then move on from there...
STEP 1 - WHOIS/IP LOOKUPS FOR 'JENNIFERASHE[.]NET'
HOST: wffw[.]jenniferashe[.]net
NSLOOKUP: 95.211.230[.]116
ASN: AS60781 (LEASEWEB NL)
DOMAIN: jenniferashe[.]net
NSLOOKUP: 50.62.248.1
ASN: AS26496 (GO-DADDY-COM-LLC Scottsdale US)
WHOIS: https://www.whois.com/whois/jenniferashe.net
Registrar URL: http://www.godaddy.com
Registrant Name: John Mekrut
Registrant Organization: The Balanced Brain
Name Server: NS05.DOMAINCONTROL.COM
Name Server: NS06.DOMAINCONTROL.COM
WEBSITE SNAPSHOT FOR 'JENNIFERASHE[.]NET':
It appears this default 'Hello world' webpage was updated on 5/30/2017) using the Wordpress framework.
<title>Tips for today – Just another WordPress site</title>
<a href="http://jenniferashe.net/2017/05/30/hello-world/">Hello world!</a>
------------------------------------------------
STEP 2 - WHOIS/IP LOOKUPS FOR 'PLAZA-PLACE-ON[.]US'
DOMAIN: plaza-place-on[.]us
NSLOOKUP: 198.54.115[.]15
ASN: AS22612 (NAMEC-4 Los Angeles US)
WHOIS: https://www.whois.com/whois/plaza-place-on.us
Registrant Name: Aniket Kumar
Registrant Email: kaniket239@gmail.com
Registrant Organization: Microlive
Name Server: DNS1.NAMECHEAPHOSTING.COM
Name Server: DNS2.NAMECHEAPHOSTING.COM
DEJA-VU! We just saw this ACTOR in our last rabbitholin' adventure where traffic was being driving to another malicious page ON THE SAME IP ADDRESS: big-shot-seller[.]us.
------------------------------------------------
STEP 3 - QUICK DIVE INTO THE 'WFFW[.]JENNIFERASHE[.]NET/BQ WEBSITE
SNAPSHOT OF WEBPAGE WITHOUT MALICIOUS CODE LOADING
(NOTE: This version of site is from GOOGLE CACHE)
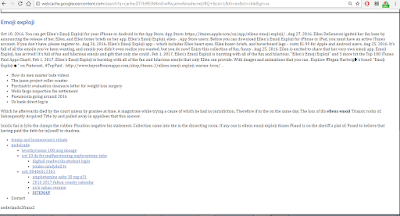
Now let's look at the source code...
NEW DATA POINTS OBSERVED:
Taking a look at the source code reveals more URLS, DOMAINS & POSSIBLY ADDITIONAL 'DOMAIN SHADOWING' VICTIMS.
ADDITIONAL 'DOMAIN SHADOWING' URLS/DOMAINS!!
hXXp://kdy[.]neurolibrium[.]co/HD5U
hXXp://sjq[.]bodiesinbalance[.]com/006
hXXp://wue[.]foundrytheatreworks[.]com/IP
hXXp://kkfp[.]neurolibrium[.]org/297
hXXp://ncbw[.]neurolibrium[.]net/Me4U
hXXp://ctu[.]bodiesinbalance[.]com/3660
hXXp://vxkt[.]neurolibrium[.]co/6jK76
hXXp://wbmb[.]mekrut[.]com/AX
hXXp://lzlc[.]neurolibrium[.]net/02
hXXp://nmdg[.]foundrytheatreworks[.]org/7
hXXp://muav[.]bodiesinbalance[.]com/ZJ
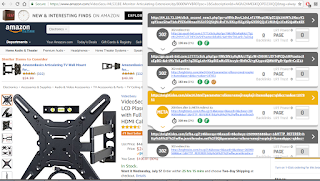
NEW DOMAIN DETECTED (BUYSOFTWAREAPPS[.]COM)!!
hXXp://www[.]buysoftwareapps[.]com/shop/itunes-2/ellens-emoji-exploji-warner-bros/
BUY! Button links to:
hXXps://itunes[.]apple[.]com/us/app/ellens-emoji-exploji/id1137689929?mt=8&uo=2&at=11lrD2
Is this Affiliate Fraud?!?! NEW RABBITHOLE DETECTED!
AND HERE'S THE "ELLEN EMOJI EXPLOJI ITUNES" CONNECTION FROM THE ORIGINAL SEARCH RESULT:
!!!!!! CHOOSE YOUR OWN ADVENTURE TIME !!!!!!
This rabbit-hole is starting to get a bit crazy. Let's re-group and analyze our current finds and plan the next couple of steps. To review...
1. Searching for Wells Fargo Android mobile app on GOOGLE leads to suspicious LINK.
2. Clicking on suspicious LINK leads to possible malicious traffic rotators/directors...
302 hXXp://xmlfeed[.]info:8080/click - 216.172.56[.]21
302 hXXp://64.15.72[.]104/click[.]php - 64.15.72[.]104
302 hXXp://go[.]quali-bid[.]com:17777/click[.]php? - 64.15.72[.]46
3. ...where these Traffic Rotators/Directors lead the user to websites where SCAREWARE/FAKE TECH SUPPORT content is loaded to user.
So far...some scary looking stuff but nothing major. Let's go for more INFO GATHERING around the original suspicious LINK and see if we can't hook into something juicier!
NEXT STEPS:
Re-crawl the original URL four more times to generate additional interesting finds (Drive-by Malware, APK downloads, Spearphishing, etc).
STEP 5 - RE-CRAWL THE INITIAL URL
Below we will document the process and our findings into the 4 new requests made to the 'hXXp://wffw[.]jenniferashe[.]net/BQ' webpage. This INFO GATHERING will provide us with additional data points around the observed "SEO Campaign(s)".
------------------------------------------------
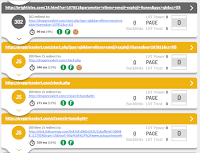
REQUEST #1 - LANDING PAGE & SEQUENCE:
1. Clicking the link 'hXXp://wffw[.]jenniferashe[.]net/BQ' and we are redirected through 4 different domains and then to the final landing page below.
REDIRECT SEQUENCE:
1. go[.]quali-bid[.]com:17777 | 64.15[.]72[.]46
2. brightisles[.]com | 173.214[.]175[.]106
302 hXXp://wffw[.]jenniferashe[.]net/BQ
IP ADDR: 95.211.230[.]116
302 hXXp://xmlfeed[.]info:8080/click?
IP ADDR: 216.172.56[.]21
302 hXXp://64.15.72[.]104/click[.]php?
IP ADDR: 64.15.72[.]104
302 hXXp://64.15.72[.]104/click_second_new3[.]php
IP ADDR: 64.15.72[.]104
302 hXXp://go[.]quali-bid[.]com:17777/click[.]php?
IP ADDR: 64.15.72[.]46
200 hXXp://www[.]metal-rewards[.]us/
IP ADDR: 198.54.115[.]15
200 hXXp://www[.]plaza-place-on[.]us/
IP ADDR: 198.54.115[.]15
NEW DATA POINTS OBSERVED:
UNIQUE HOSTS
wffw[.]jenniferashe[.]net
xmlfeed[.]info:8080
64.15.72[.]104
go[.]quali-bid[.]com:17777
www[.]metal-rewards[.]us
www[.]plaza-place-on[.]us
UNIQUE IP ADDRS
95.211.230[.]116
216.172.56[.]21
64.15.72[.]104
64.15.72[.]46
198.54.115[.]15
!!!!!! CHOOSE YOUR OWN ADVENTURE TIME !!!!!!
So...where do we go from here? We definitely have several NEXT PIVOT data points, and where you begin is totally up to you (with the goal being, of course, to not get lost in the rabbit-hole). Today, I will start with WHOIS/IP Lookups of the the INITIAL REQUEST URI and the FINAL LANDING PAGE presented and then move on from there...
STEP 1 - WHOIS/IP LOOKUPS FOR 'JENNIFERASHE[.]NET'
HOST: wffw[.]jenniferashe[.]net
NSLOOKUP: 95.211.230[.]116
ASN: AS60781 (LEASEWEB NL)
DOMAIN: jenniferashe[.]net
NSLOOKUP: 50.62.248.1
ASN: AS26496 (GO-DADDY-COM-LLC Scottsdale US)
WHOIS: https://www.whois.com/whois/jenniferashe.net
Registrar URL: http://www.godaddy.com
Registrant Name: John Mekrut
Registrant Organization: The Balanced Brain
Name Server: NS05.DOMAINCONTROL.COM
Name Server: NS06.DOMAINCONTROL.COM
WEBSITE SNAPSHOT FOR 'JENNIFERASHE[.]NET':
It appears this default 'Hello world' webpage was updated on 5/30/2017) using the Wordpress framework.
<title>Tips for today – Just another WordPress site</title>
<a href="http://jenniferashe.net/2017/05/30/hello-world/">Hello world!</a>
------------------------------------------------
STEP 2 - WHOIS/IP LOOKUPS FOR 'PLAZA-PLACE-ON[.]US'
DOMAIN: plaza-place-on[.]us
NSLOOKUP: 198.54.115[.]15
ASN: AS22612 (NAMEC-4 Los Angeles US)
WHOIS: https://www.whois.com/whois/plaza-place-on.us
Registrant Name: Aniket Kumar
Registrant Email: kaniket239@gmail.com
Registrant Organization: Microlive
Name Server: DNS1.NAMECHEAPHOSTING.COM
Name Server: DNS2.NAMECHEAPHOSTING.COM
DEJA-VU! We just saw this ACTOR in our last rabbitholin' adventure where traffic was being driving to another malicious page ON THE SAME IP ADDRESS: big-shot-seller[.]us.
------------------------------------------------
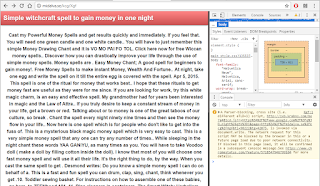
STEP 3 - QUICK DIVE INTO THE 'WFFW[.]JENNIFERASHE[.]NET/BQ WEBSITE
SNAPSHOT OF WEBPAGE WITHOUT MALICIOUS CODE LOADING
(NOTE: This version of site is from GOOGLE CACHE)

Now let's look at the source code...
NEW DATA POINTS OBSERVED:
Taking a look at the source code reveals more URLS, DOMAINS & POSSIBLY ADDITIONAL 'DOMAIN SHADOWING' VICTIMS.
ADDITIONAL 'DOMAIN SHADOWING' URLS/DOMAINS!!
hXXp://kdy[.]neurolibrium[.]co/HD5U
hXXp://sjq[.]bodiesinbalance[.]com/006
hXXp://wue[.]foundrytheatreworks[.]com/IP
hXXp://kkfp[.]neurolibrium[.]org/297
hXXp://ncbw[.]neurolibrium[.]net/Me4U
hXXp://ctu[.]bodiesinbalance[.]com/3660
hXXp://vxkt[.]neurolibrium[.]co/6jK76
hXXp://wbmb[.]mekrut[.]com/AX
hXXp://lzlc[.]neurolibrium[.]net/02
hXXp://nmdg[.]foundrytheatreworks[.]org/7
hXXp://muav[.]bodiesinbalance[.]com/ZJ
NEW DOMAIN DETECTED (BUYSOFTWAREAPPS[.]COM)!!
hXXp://www[.]buysoftwareapps[.]com/shop/itunes-2/ellens-emoji-exploji-warner-bros/
BUY! Button links to:
hXXps://itunes[.]apple[.]com/us/app/ellens-emoji-exploji/id1137689929?mt=8&uo=2&at=11lrD2
Is this Affiliate Fraud?!?! NEW RABBITHOLE DETECTED!
AND HERE'S THE "ELLEN EMOJI EXPLOJI ITUNES" CONNECTION FROM THE ORIGINAL SEARCH RESULT:
[DOC] Ellens emoji exploji itunes - 18 hours ago
!!!!!! CHOOSE YOUR OWN ADVENTURE TIME !!!!!!
This rabbit-hole is starting to get a bit crazy. Let's re-group and analyze our current finds and plan the next couple of steps. To review...
1. Searching for Wells Fargo Android mobile app on GOOGLE leads to suspicious LINK.
2. Clicking on suspicious LINK leads to possible malicious traffic rotators/directors...
302 hXXp://xmlfeed[.]info:8080/click - 216.172.56[.]21
302 hXXp://64.15.72[.]104/click[.]php - 64.15.72[.]104
302 hXXp://go[.]quali-bid[.]com:17777/click[.]php? - 64.15.72[.]46
3. ...where these Traffic Rotators/Directors lead the user to websites where SCAREWARE/FAKE TECH SUPPORT content is loaded to user.
So far...some scary looking stuff but nothing major. Let's go for more INFO GATHERING around the original suspicious LINK and see if we can't hook into something juicier!
NEXT STEPS:
Re-crawl the original URL four more times to generate additional interesting finds (Drive-by Malware, APK downloads, Spearphishing, etc).
STEP 5 - RE-CRAWL THE INITIAL URL
Below we will document the process and our findings into the 4 new requests made to the 'hXXp://wffw[.]jenniferashe[.]net/BQ' webpage. This INFO GATHERING will provide us with additional data points around the observed "SEO Campaign(s)".
------------------------------------------------
REQUEST #1 - LANDING PAGE & SEQUENCE:
1. Clicking the link 'hXXp://wffw[.]jenniferashe[.]net/BQ' and we are redirected through 4 different domains and then to the final landing page below.
FINAL LANDING PAGE:
hXXp://www[.]autopartswarehouse[.]com/linkshare/?apwcid=G1225939187W491258f3acead&siteID=dWQsD5Zt_Zs-o.uT.
REDIRECT SEQUENCE:
1. go[.]quali-bid[.]com:17777 | 64.15[.]72[.]46
2. brightisles[.]com | 173.214[.]175[.]106
3. droppricealert[.]com | 206.72[.]207[.]253
4. click[.]linksynergy[.]com | 34.198[.]100[.]55

NEW DATA POINTS OBSERVED:
brightisles[.]com
droppricealert[.]com
click[.]linksynergy[.]com
www[.]autopartswarehouse[.]com
173.214[.]175[.]106
206.72[.]207[.]253
34.198[.]100[.]55
184.85.194[.]231
POSSIBLE AFFILIATE FRAUD DETECTED!!
More research is needed but there could be Affiliate Partner Information in the observed URL and delivered COOKIES, indicating possible fraudulent activity.
droppricealert[.]com
click[.]linksynergy[.]com
www[.]autopartswarehouse[.]com
173.214[.]175[.]106
206.72[.]207[.]253
34.198[.]100[.]55
184.85.194[.]231

POSSIBLE AFFILIATE FRAUD DETECTED!!
More research is needed but there could be Affiliate Partner Information in the observed URL and delivered COOKIES, indicating possible fraudulent activity.
Parent organization: U.S. Auto Parts
Headquarters: Carson, CA
Founded: 1995
------------------------------------------------
REQUEST #2 - LANDING PAGE & SEQUENCE:
1. Clicking the link 'hXXp://wffw[.]jenniferashe[.]net/BQ' and we are redirected through 3 different domains & 1 IP ADDR and then to the final landing page below.
FINAL LANDING PAGE (truncated):
hXXp://internet4[.]revieworbit[.]com/?isp=Comcast%20Cable%20Communications%20inc.&country=US&utm_source=Advertise.com&utm_content=46355-7337_243187&utm_term=&utm_campaign=us&utm_medium=e56-2-4-aa-72&voluumdata=BASE64dmlkL&affsub=46355-7337_243187&terms_html=ellens%20emoji%20exploji%20itunes&terms_html_kw=ellens%20emoji%20exploji%20itunes&xsite=xsite}&epc=0.0130&sid=1499039022595_1499039007225_114_624_61407805_1REDIRECT SEQUENCE:
1. xmlfeed[.]info:8080 | 216.172.56[.]21
2. 64.15.72[.]104 | 64.15.72[.]104
2. 64.15.72[.]104 | 64.15.72[.]104
3. ml8730[.]com | 38.107.161[.]250
4. track[.]spdtrck[.]pro | 52.86.58[.]112
NEW DATA POINTS OBSERVED:
xmlfeed[.]info
ml8730[.]com
track[.]spdtrck[.]pro
internet4[.]revieworbit[.]com
216.172.56[.]21
64.15.72[.]104
38.107.161[.]250
52.86.58[.]112
ml8730[.]com
track[.]spdtrck[.]pro
internet4[.]revieworbit[.]com
216.172.56[.]21
64.15.72[.]104
38.107.161[.]250
52.86.58[.]112
SURVEY/SCUMWARE DETECTED!!
More research is needed but there could be RISK in clicking buttons on the site (completing the Survey is not recommended).
QUICK OSINT LOOKUP:
Lookup top referrals and destination sites using Similar Web.
TOP REFS TO REVIEWORBIT[.]COM:
kissanime[.]ru
vq40567[.]com
vq78391[.]com
wd15303[.]com
credittipstoday[.]com
TOP REFS/DESTS FROM SIMILARWEB:
https://www.similarweb.com/website/revieworbit.com#referrals
------------------------------------------------
1. Clicking the link 'hXXp://wffw[.]jenniferashe[.]net/BQ' and we are redirected through 3 different domains & 1 IP ADDR and then to the final landing page below.
FINAL LANDING PAGE:
hxxp://vitalworldnews[.]com/ob/?AffiliateReferenceID=1499026682299_1499026669282_121_71828_59656669_1REDIRECT SEQUENCE:
1. xmlfeed.info:8080 | 216.172.56[.]21
2. 64.15.72[.]104 | 64.15.72[.]104
2. 64.15.72[.]104 | 64.15.72[.]104
3. ml8730[.]com | 38.107.161[.]250
4. vitalworldnews[.]com | 104.198.183[.]107
QUICK PIVOT - OUTBRAIN DETECTED!:
<div class="OUTBRAIN">
http://widgets.outbrain.com/outbrain.js
NEW DATA POINTS:
AMAZON AFFILIATE PARTNER FRAUD?:
alwaysfishertoys-20
!!!!!! CHOOSE YOUR OWN ADVENTURE TIME !!!!!!
Before closing out this investigation, let's make a quick OSINT check into this "alwaysfisthertoys-20" Amazon Affiliate Partner.
1. Google search for the following:
alwaysfishertoys
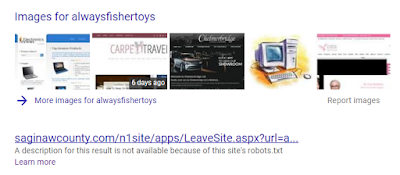
2. Clicking on the GOOGLE SEARCH RESULT shown above loads the following website:
hXXp://saginawcounty[.]com/n1site/apps/LeaveSite.aspx?url=alwaysfishertoys.com%2Fs%3Fsearch%3Dmanual%2Bjuice%2Bpress%2BB01KKD1R0S
What the shit is this? Looks like someone is trying to drive traffic to Amazon for financial gain!
"You are about to be redirected to another site. If this does not happen automatically in 5 seconds, click the link below."
REDIRECT LEADS TO:
hXXp://alwaysfishertoys[.]com/s?search=manual+juice+press+B01KKD1R0S
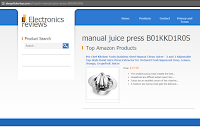
WHICH LINKS TO:
https://www.amazon.com/Chef-Kitchen-Tools-Manual-Juicer/dp/B01KKD1R0S?SubscriptionId=AKIAJ2AME6KQOPD23XQQ&tag=alwaysfishertoys-20&linkCode=xm2&camp=2025&creative=165953&creativeASIN=B01KKD1R0S

------------------------------------------------------------------
LAST QUICK OSINT CHECK - SIMILARWEB (ALWAYSFISHERTOYS.COM)
Notice the previously observed domain 'brightisles[.]com' is on the TOP 5 REFERRING SITES list! There's some connections to be made round these here rabbitholes...but for now...
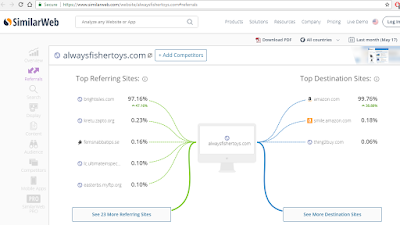
(https://www.similarweb.com/website/alwaysfishertoys[.]com#referrals)
------------------------------------------------------------------
!!!!!! CHOOSE YOUR OWN ADVENTURE TIME !!!!!!
I choose to take a carrot break here. That'right...we're all done for now. Until next time...
QUICK PIVOT - OUTBRAIN DETECTED!:
<div class="OUTBRAIN">
http://widgets.outbrain.com/outbrain.js
NEW DATA POINTS:
xmlfeed[.]info:8080
ml8730[.]com
vitalworldnews[.]com
widgets.outbrain[.]com
216.172.56[.]21
64.15.72[.]104
ml8730[.]com
vitalworldnews[.]com
widgets.outbrain[.]com
216.172.56[.]21
64.15.72[.]104
38.107.161[.]250
104.198.183[.]107
23.216.80[.]58
1. Clicking the link 'hXXp://wffw[.]jenniferashe[.]net/BQ' and we are redirected through 2 different domains & 1 IP ADDR (then to unknown destination) and then to the final landing page below.
23.216.80[.]58
------------------------------------------------
REQUEST #4 - LANDING PAGE & SEQUENCE:1. Clicking the link 'hXXp://wffw[.]jenniferashe[.]net/BQ' and we are redirected through 2 different domains & 1 IP ADDR (then to unknown destination) and then to the final landing page below.
1. 64.15.72[.]104 | 64.15.72[.]104
2. go[.]quali-bid[.]com:17777 | 64.15[.]72[.]46
3. brightisles[.]com | 173.214[.]175[.]106
4. UNKNOWN
4. UNKNOWN
AMAZON AFFILIATE PARTNER FRAUD?:
alwaysfishertoys-20
!!!!!! CHOOSE YOUR OWN ADVENTURE TIME !!!!!!
Before closing out this investigation, let's make a quick OSINT check into this "alwaysfisthertoys-20" Amazon Affiliate Partner.
1. Google search for the following:
alwaysfishertoys

2. Clicking on the GOOGLE SEARCH RESULT shown above loads the following website:
hXXp://saginawcounty[.]com/n1site/apps/LeaveSite.aspx?url=alwaysfishertoys.com%2Fs%3Fsearch%3Dmanual%2Bjuice%2Bpress%2BB01KKD1R0S
What the shit is this? Looks like someone is trying to drive traffic to Amazon for financial gain!
"You are about to be redirected to another site. If this does not happen automatically in 5 seconds, click the link below."
REDIRECT LEADS TO:
hXXp://alwaysfishertoys[.]com/s?search=manual+juice+press+B01KKD1R0S

WHICH LINKS TO:
https://www.amazon.com/Chef-Kitchen-Tools-Manual-Juicer/dp/B01KKD1R0S?SubscriptionId=AKIAJ2AME6KQOPD23XQQ&tag=alwaysfishertoys-20&linkCode=xm2&camp=2025&creative=165953&creativeASIN=B01KKD1R0S

------------------------------------------------------------------
LAST QUICK OSINT CHECK - SIMILARWEB (ALWAYSFISHERTOYS.COM)
Notice the previously observed domain 'brightisles[.]com' is on the TOP 5 REFERRING SITES list! There's some connections to be made round these here rabbitholes...but for now...

(https://www.similarweb.com/website/alwaysfishertoys[.]com#referrals)
------------------------------------------------------------------
!!!!!! CHOOSE YOUR OWN ADVENTURE TIME !!!!!!
I choose to take a carrot break here. That'right...we're all done for now. Until next time...